BSc (Hons) Ethical Hacking and Cyber Security
Introduction
With a strong emphasis on practical application of academic and theoretical aspects, this programme aims to teach the key skills and competencies required by a cybersecurity professional, using specialised physical and virtual labs. It will cover specialist security topics in the computing field, including forensics, cryptography, security management, penetration testing, reverse engineering and exploit development.
UK-specific contents may not be applicable to HK students
Ephraim Mak
BSc (Hons) Ethical Hacking and Cybersecurity
Coventry University Student Ambassador
Programme Features
Learning at Cybersecurity Centre
The Centre established by VTC at Chai Wan Campus. It plays an important role in nurturing young talents through pre-employment training for cybersecurity workforce. Students will have opportunities to attend trainings to upskill competencies of professionals through handling real scenario security incident.
Qualifications Framework
The programme is accredited by the HKCAAVQ at Hong Kong Qualification Framework (HKQF) Level 5 which is the same as that of locally accredited honours bachelor's degree programmes.
Employment
The degree qualification pitched at HKQF Level 5 are formally recognised by the HKSAR Government for employment purposes for graduate posts.
Further studies
Upon graduation, students may pursue their further studies at Master’s degree level.
Modules
- Academic Writing 3: Writing Skills for Dissert and Res Prj
-
This module offers students strategies for conceptualising, planning, drafting, revising, and editing longer assignments such as final-year projects and dissertations. Focusing on the Level 3 associated tasks of 'evaluate', 'synthesise', 'argue' and ‘reflect’, this module emphasises the place of these types of discourse and practice in academic communication. This module will be of value to students in all disciplines, and the competences they acquire and develop will contribute to their university personal development and, implicitly, to their future workplace roles that are increasingly writing intensive.
- Applied Forensics
-
Students will be exposed to industry-standard tools and methods in order to analyse and report on desktop/laptop system and mobile devices. The identification of digital evidence and its recovery and analysis in accordance with the relevant legislation and methodologies are thoroughly examined.
- Practical Cryptography
-
Students will make practical use of cryptography for encrypting, signing and verifying data in a number of forms. The underlying theory will be examined in the abstract, with a focus on practical application and developing software with cryptographic primitives.
- Security Management
-
This module aims to provide students with an in-depth understanding of information security concepts and an understanding of how they are applied and evaluated, taking into consideration customer and user needs. The importance of a security policy and security management is considered. Students will gain an understanding of the threats posed to organisations and businesses due to security risks and will be introduced to handling and mitigating such risks. The module will also introduce the concept of continuity planning, as well as relevant prevention and recovery techniques to deal with potential threats. Students will develop comprehensive understanding of the legal, policy and technical approaches that are necessary to mitigate relevant risks.
- Reverse Engineering
-
This module studies techniques for examining programs and protocols where the source code may not be available, by investigating the way that software behaves with a given set of inputs, and examining the binary representation of a program with the aim of developing an understanding of the original program. Additionally, methods for the identification, and analysis of malicious code are examined.
- Exploit Development
-
In this module students will examine how vulnerabilities in software can be exploited to compromise a system or network. Students will examine how "off the shelf" exploit code can be detected by security mechanisms, and how common protection techniques such as Antivirus and firewalls can be bypassed. Additionally, the students will examine how exploit code is developed on common operating systems.
- Security Audit and Monitoring
-
This module introduces the concepts of security audit processes as well as formal assessment methodologies. The module is designed to equip students with the skills to plan and perform system and penetration testing to effectively identify evidence of vulnerabilities, explain the vulnerabilities and make recommendations of how to mitigate them. The module also aims to give an in-depth understanding of intrusion detection systems for monitoring and identification of malicious activities and policy violations. The module aims to provide the students with awareness of the aspects related to security incident response and handling and enable them to develop the ability to evaluate and apply appropriate methodologies of managing relevant investigations.
- Cyber Security Project
-
This module provides students with the opportunity and support to conduct primary and secondary research in cyber security. Students will undertake a substantial project which will exercise the in-depth technical, problem-solving, creative and other skills required of a professional practitioner. Students will be required to ensure that their work conforms to appropriate codes of practice and meets the ethical requirements of the University. Successful completion of the project will require methodical planning, record keeping, self-management, effective communication, execution and delivery of an agreed artefact or piece of research. Support and guidance will be provided by a project supervisor who will be the primary point of contact for a student on this module.
We regularly review our course content, to make it relevant and current for the benefit of our students. For these reasons, course modules may be updated, please contact us for the latest information.
We regularly review our course content, to make it relevant and current for the benefit of our students. For these reasons, course modules may be updated, please contact us for the latest information.
Assessment
Reports, phase test and final project, etc.
QF Level
|
QF Level : Level 5
|
|
|
Importance of choosing a non-local top-up with QF Level 5Employment
|
|
Entry Requirements
OR
OR
|
English Proficiency Requirements
OR
*Subject to final approval by Coventry University |
Fees
- Application Fee : HK$200 (No application fee before the deadline!)
- Registration Fee : HK$3,500
- Tuition Fee : HK$84,720 by 3 instalments
Scholarships
A variety of attractive scholarships are available to current and graduating SHAPE students
Financial Aids
The following HKSAR Government financial assistance schemes are available to eligible students who pursue this programme at SHAPE:
|
|
||
For details including eligibility and subsidy amount, please refer to the hyperlink of each scheme.
Career Prospects
The practical nature of this programme places an emphasis on students' future employability, developing a wide range of technical, analytical, design and professional skills. Graduates will be able to find employment in ethical hacking and penetration testing roles, malware and software security analysis, telecoms security, digital forensics and evidence gathering, network and security administration within organisations, government organisations and insurance companies.
 |
"Through this programme and guidance by SHAPE lecturers, I have learnt the latest development in the IT security industry. I enjoyed the “System Security” module the most which covers essential knowledge at the workplace like cryptography, website protection and risk management. I am also very impressed with SHAPE lecturers that they shared extensive real-world cases in hacking. This is a very practical programme and it helped me to get employed shortly after graduation." Yuen Chun Ho BSc (Hons) Ethical Hacking and Cybersecurity
|
Further Studies
Having been recognised at QF Level 5, this top-up degree programme meets the standard of locally-accredited bachelor's degree programmes. Upon graduation, students can pursue their further studies at Master’s degree level in Hong Kong or other regions.
Student Awards
2nd Runner Up - 粵港澳(大灣區)模擬網絡防衛比賽2023
Chu Leung Shing, Leung Suet Yi, Ng Yu Tung, Wong Chi Hin
3rd Runner Up - Greater Bay Area Cybersecurity Competition 2023 organized
Chu Leung Shing, Ng Yu Tung, Wong Chi Hin
1st Runner Up - Cybersecurity Blue Team Competition 2021
Chiu Ka Leung, Lam Chin Wang, Lam Wui Kin, Leung Chak Ching, Tam Lok Hang
Champion - Cybersecurity Purple Team Competition 2022
Mak Ka Hung, Thian Chun Yue

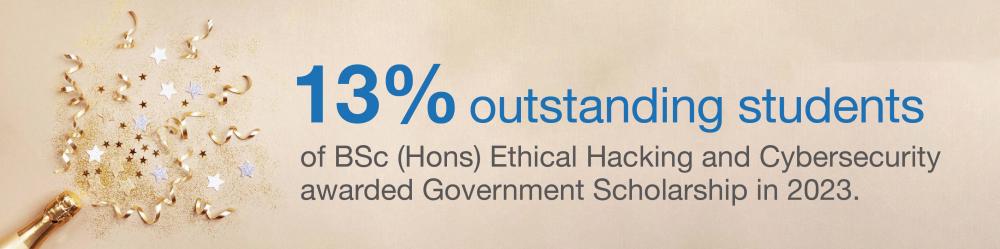
| Student | Awards |
| Ng King Hei | HKSAR Government Outstanding Performance Scholarship 2022-23 |
| Thian Chun Yue | HKSAR Government Outstanding Performance Scholarship 2021-22 |
| Yuen Chun Ho | HKSAR Government Outstanding Performance Scholarship 2021-22 |
Graduation Ceremony










